list some of the security concerns of an rfid system In this type of attack, an attacker tries to insert system commands to the RFID system instead of sending normal data.an example of RFID insert attack is that a tag carrying system . See more Where can I find a video tutorial on how to install NFC? How to Install Geotab IOX .
0 · rfid security problems
1 · rfid privacy and security issues
2 · rfid is vulnerable to
3 · rfid disadvantages
4 · problems with rfid technology
5 · problems with rfid
6 · is rfid dangerous
7 · compliance issues with rfid bands
RC522 NFC/RFID¶. The rc522 component allows you to use RC522 NFC/RFID controllers (datasheet, Ali Express) with ESPHome.ESPHome can read the UID from the tag. Every NFC/RFID tag has a unique “UID” value assigned at the .
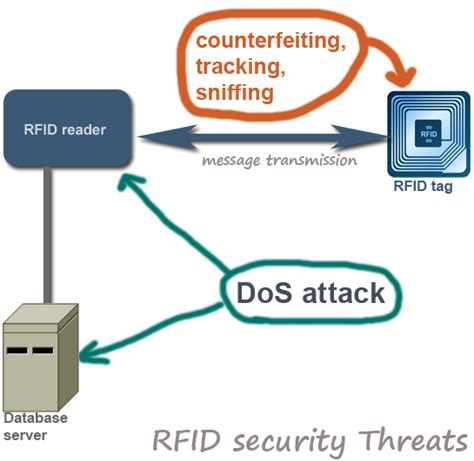
Like any other security devices and mechanism RFID is not flawless. Despite its widespread application and usage, RFID poses security threats and challenges that need to be addressed properly before deployment. This post aims to highlight several important RFID related security issues. Like any other . See moreRFID Counterfeiting: depending on the computing power, RFID can be classified into three categories: See moreIn a spoofing attack, the attacker masquerade as a legitimate user of the system. The attacker can pose himself as an authorized Object Naming Service user or database user. If an attacker can successfully get access to the system with his spoofed . See more
In this type of attack, an attacker tries to insert system commands to the RFID system instead of sending normal data.an example of RFID insert attack is that a tag carrying system . See moreAs you know that repudiation means when as user officially deny that he has done an action and we have no way to verify that whether he has performed that particular action. In the case of . See morecurrent RFID protocols are designed to optimize performance, with lesser attention paid to resilience and security. Consequently, most RFID systems are inherently insecure. In this .Despite its widespread application and usage, RFID poses security threats and challenges that need to be addressed properly before deployment. This post aims to highlight several .
current RFID protocols are designed to optimize performance, with lesser attention paid to resilience and security. Consequently, most RFID systems are inherently insecure. In this .
rfid security problems
Below are 7 known security attacks hackers can perform on an RFID system. 1. Reverse Engineering. Like most products, RFID tags and readers can be reverse engineered; . By closely monitoring the power consumption levels of RFID tags, hackers can fool your systems. With some ingenuity and a cell phone bad actors can perform an RFID hack . Part 2 examines some of the more common security and privacy concerns associated with RFID, primarily related to retail and consumer applications. What is RFID? This publication seeks to assist organizations in understanding the risks of RFID technology and security measures to mitigate those risks. It provides practical, real-world .
“Security issues in RFID system” presents various attacks possible on RFID devices. This section includes the attacks based on the CIA (confidentiality, integrity, and .
rfid privacy and security issues
RFID systems are vulnerable to denial of service (DoS) attacks by disrupting communication between tags and readers. Malicious actors overwhelm these two with .However, RFID systems also raise serious privacy and security concerns. This article offers a brief review of the main threats to RFID systems and proposes a methodology for qualitatively .
Within less than a decade, a large number of research papers dealing with security issues of RFID technology have appeared. In this paper we want to provide some thoughts on .
Despite its widespread application and usage, RFID poses security threats and challenges that need to be addressed properly before deployment. This post aims to highlight several .current RFID protocols are designed to optimize performance, with lesser attention paid to resilience and security. Consequently, most RFID systems are inherently insecure. In this .
Below are 7 known security attacks hackers can perform on an RFID system. 1. Reverse Engineering. Like most products, RFID tags and readers can be reverse engineered; . By closely monitoring the power consumption levels of RFID tags, hackers can fool your systems. With some ingenuity and a cell phone bad actors can perform an RFID hack . Part 2 examines some of the more common security and privacy concerns associated with RFID, primarily related to retail and consumer applications. What is RFID?
does my phone have a nfc reader
This publication seeks to assist organizations in understanding the risks of RFID technology and security measures to mitigate those risks. It provides practical, real-world . “Security issues in RFID system” presents various attacks possible on RFID devices. This section includes the attacks based on the CIA (confidentiality, integrity, and .
RFID systems are vulnerable to denial of service (DoS) attacks by disrupting communication between tags and readers. Malicious actors overwhelm these two with .However, RFID systems also raise serious privacy and security concerns. This article offers a brief review of the main threats to RFID systems and proposes a methodology for qualitatively .
electron read nfc

rfid is vulnerable to
In the example above “your.uniqueapp.nfc” can be “com.your.package.name.nfc”. The idea of having a unique Mime Type on the NFC tags is to prevent the device from having to choose between launching .
list some of the security concerns of an rfid system|rfid disadvantages