copy private key from smart card It is possible to export the certificate and copy to your laptop but to identify, sign or decrypt it is necessary to use the private key. The private key is usually generated on the smartcard and is not extractable. Java 64.2%. Kotlin 35.8%. e-Passport NFC Reader Android app. .
0 · piv private key extract
1 · piv private key
Find many great new & used options and get the best deals for Nintendo 3ds NFC Reader/writer at the best online prices at eBay! Free shipping for many products!The Nintendo 3DS is a breakthrough in portable entertainment, a truly cutting .
It is possible to export the certificate and copy to your laptop but to identify, sign or decrypt it is necessary to use the private key. The private key is usually generated on the smartcard and is not extractable.
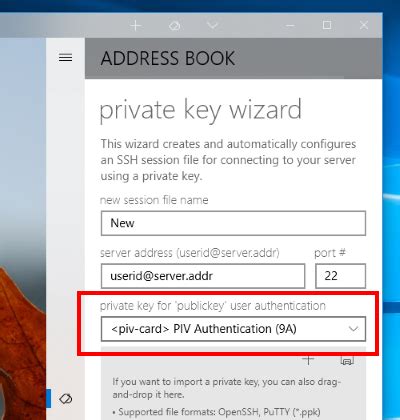
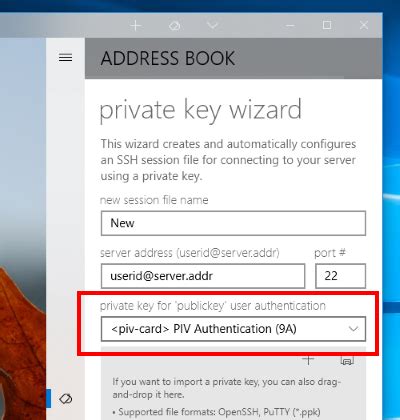
Using PuTTy integration, it works great for SSH authentication. I was under the impression that .
piv private key extract
piv private key
You can't extract the private key out of a PIV smartcard, as this is done as a . It is possible to export the certificate and copy to your laptop but to identify, sign or decrypt it is necessary to use the private key. The private key is usually generated on the smartcard and is not extractable.Using PuTTy integration, it works great for SSH authentication. I was under the impression that you shouldn't be able to export the private key if it is safely stored on the smart card (YubiKey), as crypto operations are handed off to the cards onboard processor to avoid it leaving. You can't extract the private key out of a PIV smartcard, as this is done as a secure vault for the private key. But you can use a Putty agent compatible with Pageant which uses a PIV card as a secure key storage, that's the clear goal of PIVageant, that my company developed.
Secret keys cannot be exported from OpenPGP smart cards -- that's the very idea behind them. If you created the key on a computer and imported it to the smart card, use the backup to copy it to the Yubikey. Otherwise, you'll have to create a new key. This is what the United States Department of Defense (DoD) uses all around. You could look around on the web to see where you can get a free copy. Importing a GPG (openPGP) Certificate. Transferring, or importing, the private onto the Smartcard is a bit easier than importing PIV certificates. You can use the usual gpg tools. gpg --card-statusConsider you lost your laptop with sensitive data and your smart card that contains the private key for your GnuPG and Truecrypt accounts. The smartcard is secured with a 8-digit PIN. Exporting a certificate with Private Key. On the workstation where you enrolled the smart card certificates, choose Start, choose Run, and then in the Open box, type MMC. Choose OK. On the Console page, on the File menu, select Add/Remove Snap in.
Use the IX509Enrollment->CreateRequest method with XCN_CRYPT_STRING_BINARY to obtain the serialized request. Depending on how you initialized your instance of IX509Enrollement, you can get a PKCS#10 request or a CMC . I have generated a pair of RSA keys on a smart card with OpenSC tools and retrieved it as wrapped key blob encrypted with DKEK key: Software can ask the smart card to perform cryptographic operations on its behalf without disclosing the key to the computer (in fact, there is no reasonable way to extract the private key from a smart card). To prevent unauthorized use the smart code requires the user provide a short PIN.
It is possible to export the certificate and copy to your laptop but to identify, sign or decrypt it is necessary to use the private key. The private key is usually generated on the smartcard and is not extractable.Using PuTTy integration, it works great for SSH authentication. I was under the impression that you shouldn't be able to export the private key if it is safely stored on the smart card (YubiKey), as crypto operations are handed off to the cards onboard processor to avoid it leaving. You can't extract the private key out of a PIV smartcard, as this is done as a secure vault for the private key. But you can use a Putty agent compatible with Pageant which uses a PIV card as a secure key storage, that's the clear goal of PIVageant, that my company developed.
Secret keys cannot be exported from OpenPGP smart cards -- that's the very idea behind them. If you created the key on a computer and imported it to the smart card, use the backup to copy it to the Yubikey. Otherwise, you'll have to create a new key. This is what the United States Department of Defense (DoD) uses all around. You could look around on the web to see where you can get a free copy. Importing a GPG (openPGP) Certificate. Transferring, or importing, the private onto the Smartcard is a bit easier than importing PIV certificates. You can use the usual gpg tools. gpg --card-statusConsider you lost your laptop with sensitive data and your smart card that contains the private key for your GnuPG and Truecrypt accounts. The smartcard is secured with a 8-digit PIN. Exporting a certificate with Private Key. On the workstation where you enrolled the smart card certificates, choose Start, choose Run, and then in the Open box, type MMC. Choose OK. On the Console page, on the File menu, select Add/Remove Snap in.
Use the IX509Enrollment->CreateRequest method with XCN_CRYPT_STRING_BINARY to obtain the serialized request. Depending on how you initialized your instance of IX509Enrollement, you can get a PKCS#10 request or a CMC . I have generated a pair of RSA keys on a smart card with OpenSC tools and retrieved it as wrapped key blob encrypted with DKEK key:
Auburn: Alabama: Auburn University: 91.1 FM WJAB: Huntsville: Alabama: Alabama A&M University: 90.9 FM WLJS: Jacksonville: . Virginia: Virginia Tech: 90.7 FM .
copy private key from smart card|piv private key extract