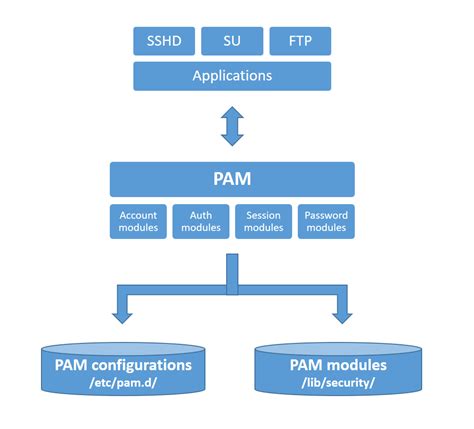
authentication method is required for the use of smart cards For smart cards, Windows supports a provider architecture that meets the secure authentication requirements and is extensible so that you can include custom credential providers. This topic includes information about: Credential provider architecture; Smart card subsystem architecture; Credential provider architecture The same logo should be visible on retailers’ contactless-capable payment readers. When you’re ready to pay, simply wave or tap the .Customers load their American Express® Card information onto an NFC-enabled phone: NFC .
0 · module 12 authentication test
1 · module 12 authentication
The number printed on the is probably related to the account detail of the contactless credit or debit card, these are stored on the card in the memory of the card and .
Which of the following is required for two-factor authentication? [Choose all that apply] - USB drive - Password key - Password - Smart cardWhich of the following is required for two-factor authentication? [Choose all that apply] - USB drive - Password key - Password - Smart cardCertificate Requirements and Enumeration: Learn about requirements for smart card certificates based on the operating system, and about the operations that are performed by the operating system when a smart card is inserted into the computer.For smart cards, Windows supports a provider architecture that meets the secure authentication requirements and is extensible so that you can include custom credential providers. This topic includes information about: Credential provider architecture; Smart card subsystem architecture; Credential provider architecture
Microsoft Entra users can authenticate using X.509 certificates on their smart cards directly against Microsoft Entra ID at Windows sign-in. There's no special configuration needed on the Windows client to accept the smart card authentication. Smart card authentication is a method that employs the embedded chip in the card to verify the identity of the user certificates. The chip can generate or store authentication data through cryptographic algorithms that a reader can verify. Smart card authentication is a method that employs the embedded chip in the card to verify the identity of the user certificates. The chip can generate or store authentication data through cryptographic algorithms that a reader can verify.Smart Card Authentication is a means of verifying users into enterprise resources such as workstations and applications using a physical card in tandem with a smart card reader and software on the workstation.
Authentication Steps: The user puts the smart card into a card reader hooked up to the device or system they want to use. The card reader talks to the smart card and asks the user to enter a password number or use their body marks to prove who they are.Certificate-based authentication is an encrypted method that enables devices and people to identify themselves to other devices and systems. Two common examples are a smart card or when an employee’s device sends a digital certificate to a network or server.In order to authenticate with a smart card, the user needs to be in physical possession of the card and the secrets it carries (something the user has – first factor), and has to know the PIN that unlocks the card (something the user knows – second factor), hence providing two factor authentication. Can a hard token be duplicated?Which of the following is required for two-factor authentication? [Choose all that apply] - USB drive - Password key - Password - Smart card
module 12 authentication test
Certificate Requirements and Enumeration: Learn about requirements for smart card certificates based on the operating system, and about the operations that are performed by the operating system when a smart card is inserted into the computer.
For smart cards, Windows supports a provider architecture that meets the secure authentication requirements and is extensible so that you can include custom credential providers. This topic includes information about: Credential provider architecture; Smart card subsystem architecture; Credential provider architecture Microsoft Entra users can authenticate using X.509 certificates on their smart cards directly against Microsoft Entra ID at Windows sign-in. There's no special configuration needed on the Windows client to accept the smart card authentication.
Smart card authentication is a method that employs the embedded chip in the card to verify the identity of the user certificates. The chip can generate or store authentication data through cryptographic algorithms that a reader can verify. Smart card authentication is a method that employs the embedded chip in the card to verify the identity of the user certificates. The chip can generate or store authentication data through cryptographic algorithms that a reader can verify.Smart Card Authentication is a means of verifying users into enterprise resources such as workstations and applications using a physical card in tandem with a smart card reader and software on the workstation. Authentication Steps: The user puts the smart card into a card reader hooked up to the device or system they want to use. The card reader talks to the smart card and asks the user to enter a password number or use their body marks to prove who they are.
module 12 authentication
Certificate-based authentication is an encrypted method that enables devices and people to identify themselves to other devices and systems. Two common examples are a smart card or when an employee’s device sends a digital certificate to a network or server.
smart i cards mumbai
Click LOAD TAG to load Amiibo data of the villager you want.; Click SAVE TAG to save chosen Amiibo data on to the tag of your choice. *Be aware that the NFC tags are NOT re-writable in this case, as official Nintendo Amiibos also lock in .
authentication method is required for the use of smart cards|module 12 authentication test