which type of authentication includes smart cards Authentication by OWNERSHIP is based on something you have, such as a smart card, a key, a badge, or either a synchronous or asynchronous token.
There are a couple of NFC readers that will be able to read unencrypted cards. I personally use .
0 · windows 10 smart card setup
1 · what is smart card authentication
2 · what is an example of two factor authentication 2fa
3 · what is an example of a logical access control
4 · true or false a smart card is an example of a logical access control
5 · smart card based authentication
6 · smart card authentication step by
7 · authenticate using your smart card
What do the Animal Crossing NFC Cards do? The Animal Crossing NFC cards .
Authentication by OWNERSHIP is based on something you have, such as a smart card, a key, a badge, or either a synchronous or asynchronous token.Authentication by characteristics/biometrics is based on something you have, such .
how to read and rfid with out a loop
Study with Quizlet and memorize flashcards containing terms like What is an .Authentication by characteristics/biometrics is based on something you have, such as a smart card, a key, a badge, or either a synchronous or asynchronous token.Study with Quizlet and memorize flashcards containing terms like What is an example of a logical access control?, The ___________ is the central part of a computing environment's hardware, .
Authentication by OWNERSHIP is based on something you have, such as a smart card, a key, a badge, or either a synchronous or asynchronous token.
how to read rfid tags using vb net
Authentication by characteristics/biometrics is based on something you have, such as a smart card, a key, a badge, or either a synchronous or asynchronous token.Study with Quizlet and memorize flashcards containing terms like What is an example of a logical access control?, The ___________ is the central part of a computing environment's hardware, software, and firmware that enforces access control., Which type of authentication includes smart cards? and more.Smart cards may provide strong security authentication for single sign-on (SSO) within organizations. Numerous nations have deployed smart cards throughout their populations. The universal integrated circuit card (UICC) for mobile phones, installed as pluggable SIM card or embedded eSIM, is also a type of smart card.Certificate-based authentication is an encrypted method that enables devices and people to identify themselves to other devices and systems. Two common examples are a smart card or when an employee’s device sends a digital certificate to a network or server.
how to read data from rfid rc522
Using a smart card in conjunction with a password can add an extra layer of security to protect sensitive patient or customer data. An additional layer of security can be provided here by AI, both through scanning for compromised devices as well as performing risk-based authentication.
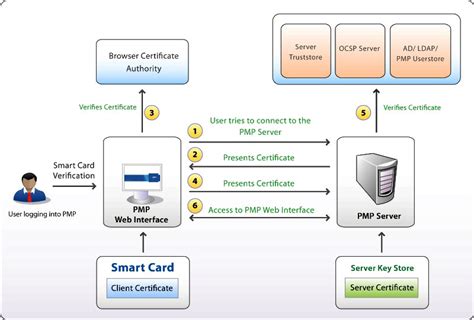
Smart Card Authentication is a means of verifying users into enterprise resources such as workstations and applications using a physical card in tandem with a smart card reader and software on the workstation.A smart card is a secure microcontroller that is typically used for generating, storing and operating on cryptographic keys. Smart card authentication provides users with smart card devices for the purpose of authentication. Users connect their smart card to a host computer. Token-based authentication enables users to log in to accounts using a physical device, such as a smartphone, security key or smart card. It can be used as part of MFA or to provide a passwordless experience. Pick the right kind of smart card: Choose a smart card type based on how much it can store, its security, and if it works with your things. Also pick card readers: Choose readers that work with the card type and security you need.
Authentication by OWNERSHIP is based on something you have, such as a smart card, a key, a badge, or either a synchronous or asynchronous token.
Authentication by characteristics/biometrics is based on something you have, such as a smart card, a key, a badge, or either a synchronous or asynchronous token.
Study with Quizlet and memorize flashcards containing terms like What is an example of a logical access control?, The ___________ is the central part of a computing environment's hardware, software, and firmware that enforces access control., Which type of authentication includes smart cards? and more.Smart cards may provide strong security authentication for single sign-on (SSO) within organizations. Numerous nations have deployed smart cards throughout their populations. The universal integrated circuit card (UICC) for mobile phones, installed as pluggable SIM card or embedded eSIM, is also a type of smart card.
windows 10 smart card setup
what is smart card authentication
Certificate-based authentication is an encrypted method that enables devices and people to identify themselves to other devices and systems. Two common examples are a smart card or when an employee’s device sends a digital certificate to a network or server. Using a smart card in conjunction with a password can add an extra layer of security to protect sensitive patient or customer data. An additional layer of security can be provided here by AI, both through scanning for compromised devices as well as performing risk-based authentication.
Smart Card Authentication is a means of verifying users into enterprise resources such as workstations and applications using a physical card in tandem with a smart card reader and software on the workstation.
what is an example of two factor authentication 2fa
A smart card is a secure microcontroller that is typically used for generating, storing and operating on cryptographic keys. Smart card authentication provides users with smart card devices for the purpose of authentication. Users connect their smart card to a host computer. Token-based authentication enables users to log in to accounts using a physical device, such as a smartphone, security key or smart card. It can be used as part of MFA or to provide a passwordless experience.
how to protect credit card with rfid
how.to get zips rfid card
Sunday, January 9, 1994. 1993 NFC Wild Card Game; Sun 1/9 1 2 3 4 FINAL; Minnesota (9-7): 0: Pass
which type of authentication includes smart cards|what is an example of a logical access control